
A hybrid espionage/influence campaign conducted by the Russian threat group UNC5812 targeting Ukrainian military recruits using Windows and Android malware has been uncovered.
According to Google Threat Intelligence, the campaign impersonated a “Civil Defense” persona along with a website and a dedicated Telegram channel to distribute malware through a fake recruitment avoidance app that researchers dubbed “Sunspinner.”
This campaign targets Windows and Android devices using platform-specific malware, providing data theft and real-time spying capabilities for attackers.
While Google has put safeguards in place to thwart malicious activity, this operation highlights Russia’s continued use and extensive capabilities in the cyberwarfare arena.
Fake “civil defense” persona
The UNC5812 persona does not attempt to impersonate any Ukrainian civil defense or government agency, but instead is promoted as a legitimate, Ukrainian-friendly organization that provides useful software tools and advice to Ukrainian conscripts.
This person uses Telegram channels and a website to engage with potential victims and tell a story that opposes Ukraine’s recruitment and mobilization efforts, with the aim of inciting public distrust and resistance.
When Google discovered the campaign on September 18, 2024, the “Civil Defense” channel on Telegram had 80,000 subscribers.
Source: Google
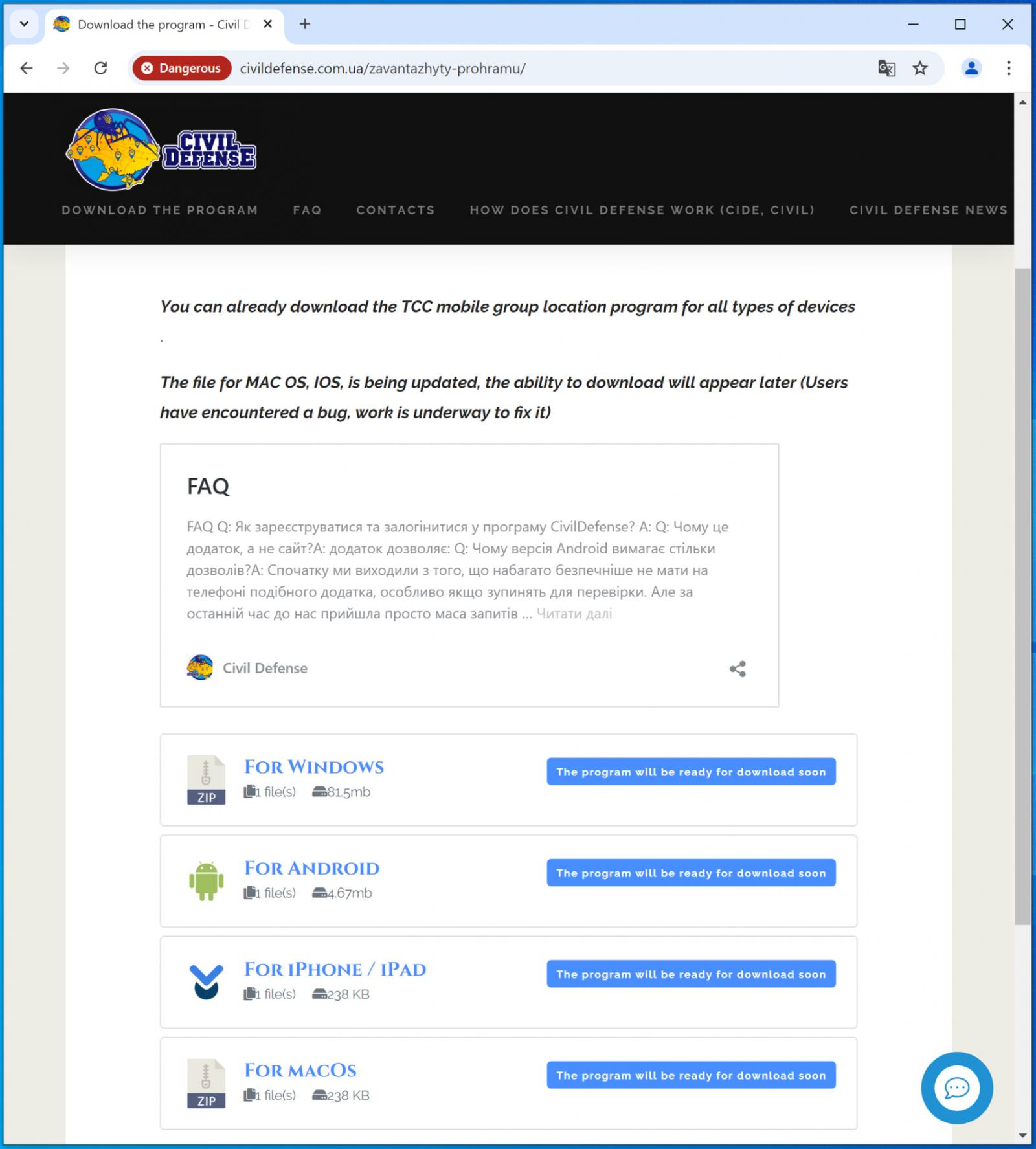
Users who are tricked into visiting the Civil Defense website are directed to a download page for a malicious application that is advertised as a crowdsourced mapping tool. This tool allows users to track and evade the location of recruiters.
Google calls the app “Sunspinner,” and it shows a map with markers, but Google claims the data is fabricated. The app’s sole purpose is to hide malware installations that occur in the background.
Source: Google
Drops Windows and Android malware.
The fake app offers downloads for Windows and Android, but Apple platforms are not yet supported as it promises to add iOS and macOS soon as well.
Windows downloads install Pronsis Loader, a malware loader that retrieves additional malicious payloads from UNC5812’s servers, including “PureStealer,” which steals product information.
PureStealer targets information stored in web browsers, including account passwords, cookies, cryptocurrency wallet details, email clients, and messaging app data.
On Android, downloaded APK files drop CraxsRAT, another commercially available backdoor.
CraxsRAT allows an attacker to track a victim’s location in real time, record keystrokes, activate voice recordings, obtain contact lists, access SMS messages, extract files, and steal credentials. can be collected.
In order to carry out these malicious activities unchecked, the app tricks users into disabling Google Play Protect, Android’s built-in anti-malware tool, and manually granting dangerous permissions.

Source: Google
Google has updated protections in Google Play to detect and block Android malware early, and added domains and files related to campaigns to Chrome’s Safe Browsing feature.
A complete list of indicators of compromise related to the latest UNC5812 campaign is available here.


