
A new version of the FakeCall malware for Android hijacks outgoing calls from users to banks and redirects them to the attacker’s phone number instead.
The goal of the latest version is still to steal sensitive information and money from people’s bank accounts.
FakeCall (or FakeCalls) is a banking Trojan that focuses on voice phishing, where victims are fooled by a fraudulent phone call that impersonates their bank and asks them to provide sensitive information.
Kaspersky first reported this Trojan in April 2022. The Trojan horse featured a realistic-looking call interface to trick victims into believing they were on the phone with their bank.
CheckPoint’s March 2023 report warned that FakeCall is now impersonating more than 20 financial institutions, offering low-interest loans to targets, and has new evasion mechanisms to reduce detection rates.
In addition to vishing (voice phishing), FakeCall can also capture live audio and video streams from infected devices, allowing attackers to steal sensitive data without victim interaction.
call hijacking
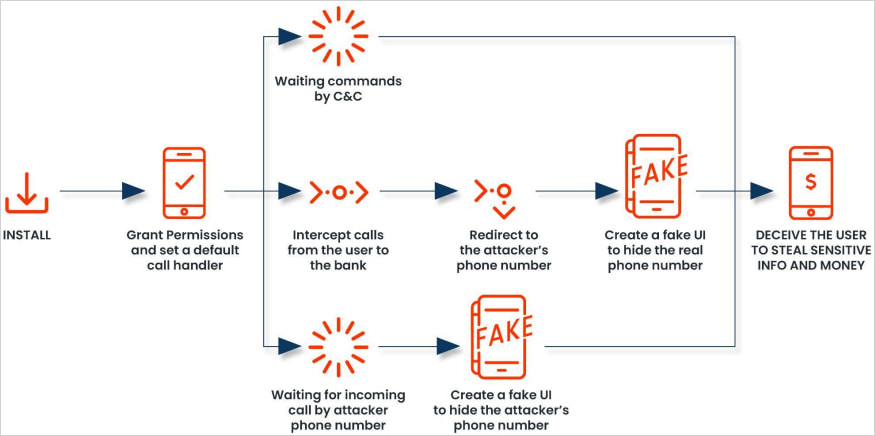
In previous versions, FakeCall prompted users to impersonate a financial institution and call their bank from within the app. A fake screen displaying the bank’s real number was then overlaid while the victim was connected with the scammer.
In the latest version analyzed by Zimperium, the malicious app sets itself as the default call handler and asks the user to approve this action when installing the application via an Android APK.
Android call handlers manage incoming and outgoing calls and essentially serve as the main interface for dialing, connecting, and ending calls.
When the malware asks the user to set it as the default call handler, it obtains permission to intercept and manipulate both outgoing and incoming calls.
The fake call interface mimics the real Android dialer and displays authentic contact information and names, increasing the level of deception to the point where it is difficult for victims to notice.
What makes this malware so dangerous is that when a user attempts to call a financial institution, the malware secretly hijacks the call and redirects it to the attacker’s phone number instead.
“When an infected individual attempts to contact a financial institution, the malware redirects the call to a fraudulent number controlled by the attacker,” Zimperium’s new report explains.
“The malicious app tricks users into displaying a fake UI that looks like a legitimate Android calling interface that displays a real bank phone number.”
“The malware’s fake UI mimics a real banking experience, so the victim is unaware of its operations and allows the attacker to extract sensitive information or gain unauthorized access to the victim’s financial accounts. becomes possible.
Source: Zimperium
New features and improvements
Despite the increased code obfuscation, Zimperium also found that the latest version of FakeCall has added several improvements and attack mechanisms, some of which are still in development. did.
First, FakeCall added a Bluetooth listener and a screen status monitor, neither of which have any malicious functionality yet.
The malware now leverages Android accessibility services to gain extensive control over the user interface, allowing it to monitor dialer activity, automatically grant permissions, and simulate user actions such as clicks and gestures. It will be.
The new phone listener service establishes a communication channel with the attacker’s command and control (C2) server and performs various actions, including obtaining device location, deleting apps, recording audio or video, and editing contacts. Allows you to issue commands to run .
The new commands added in the latest variants are:
- Set the malware as the default call handler.
- Start live streaming your device’s screen content.
- Take a screenshot of your device’s display.
- Unlock your device if it’s locked and temporarily turn off auto-lock.
- Use accessibility services to mimic pressing the home button.
- Deletes the specified image from the C2 server.
- Access, compress, and upload images and thumbnails from your storage, specifically targeting the DCIM folder for photos.
These additions indicate that FakeCall is under active development and its operators are working to make it a more evasive and powerful banking Trojan.
Zimperium has published a list of indicators of compromise (IoCs), including app package names and APK checksums, to help users avoid malicious apps that carry malware. However, these are frequently modified by threat actors.
As always, we recommend that users avoid manually installing Android apps via APKs and instead install them from Google Play. Malware can still infiltrate Google services, but Google Play Protect can remove it if detected.

